Advanced Application Security Solutions for Unparalleled Mobile App Protection
Inject powerful protection into your Android and iOS app without changing your code or affecting software functionality.Nexoya Technologies provides a widespread suite of Mobile Application Security Solution that keeps you safe from reverse engineering, application repackaging, dynamic modification, man in the device, emulators & debuggers, rooted jailbroken. Vulnerabilities increase the risk of data breaches, financial loss, and in the most extreme circumstances can even cause fatalities. Mobile Application Security Solution will reduce the risk of these incidents.
Explore our comprehensive application security solutions designed to safeguard your digital assets. From robust threat detection to proactive defense mechanisms, trust Nexoya to fortify your mobile applications and ensure a secure digital experience for your users.
There are an estimated 7.3 billion mobile devices in service for the 7 billion people in the world. In 2018, mobile apps were downloaded onto user devices over 205 billion times. According to Juniper Research, the number of people using mobile banking apps is approaching two billion—around 40 percent of the world’s adult population.
Developers pay painstaking attention to software design in order to give us a smooth and convenient experience. People gladly install mobile apps and provide personal information, but rarely stop to think about the security implications.
Impact of Weak Mobile App Security
Hackers gain login credentials of any website or device; for example, email, banking, social networking websites, etc. Anubis banking Trojan is a notorious example in this category, which enters the user’s device by downloading compromised apps, some of which are even hosted on the official app stores of Android. Once a device is infected, the Trojan forces it to send and receive SMSes, read contact lists, request permission to access device location, allow push notifications, and determine the IP address of the mobile connection along with access to personal files on the mobile device.
In May 2019, WhatsApp acknowledged that its app was vulnerable to spyware from an Israeli firm NSO group that could infect a mobile device simply by calling a user on WhatsApp from an unknown number.
Hackers can gain credit and debit card numbers to make bank transactions, particularly in cases where a one-time password is not required. Researchers from Kaspersky discovered a new version of the banking Trojan called Ginp, which could steal user credentials and credit card information from a user’s device. Its ability to take control of the SMS feature of the device allows it to manipulate banking functions. Its code was found to be manipulating 24 apps of Spanish banks.


Loopholes in Mobile App Security
Mobile apps are not designed to serve as anti-viruses or to transmit data securely over the internet. Rather they focus on a smooth interface and provide the best functionality to users. Similarly installing an antivirus app may secure the network and prevent attacks on a device, but it cannot provide protection against weak passwords or a poorly designed app.
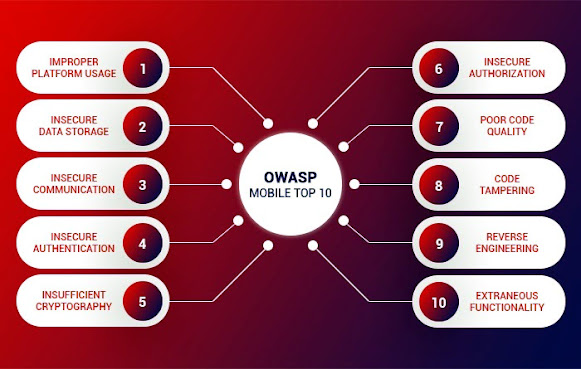
Most of the common security lapses are documented by industry experts under the aegis of The Open Web Application Security Project (OWASP) for reference for developers. Its popular list OWASP Mobile Top 10 comprehensively builds on the pooled knowledge of industry experts about the present and developing attack vectors on mobile devices.