New Security Realities of COVID-19 World
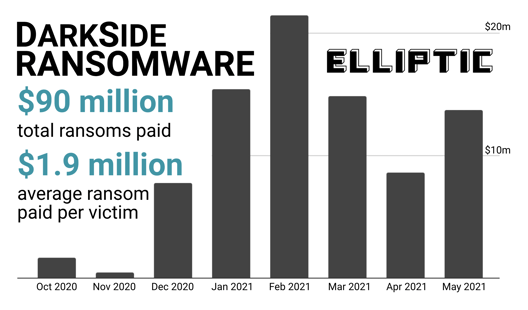
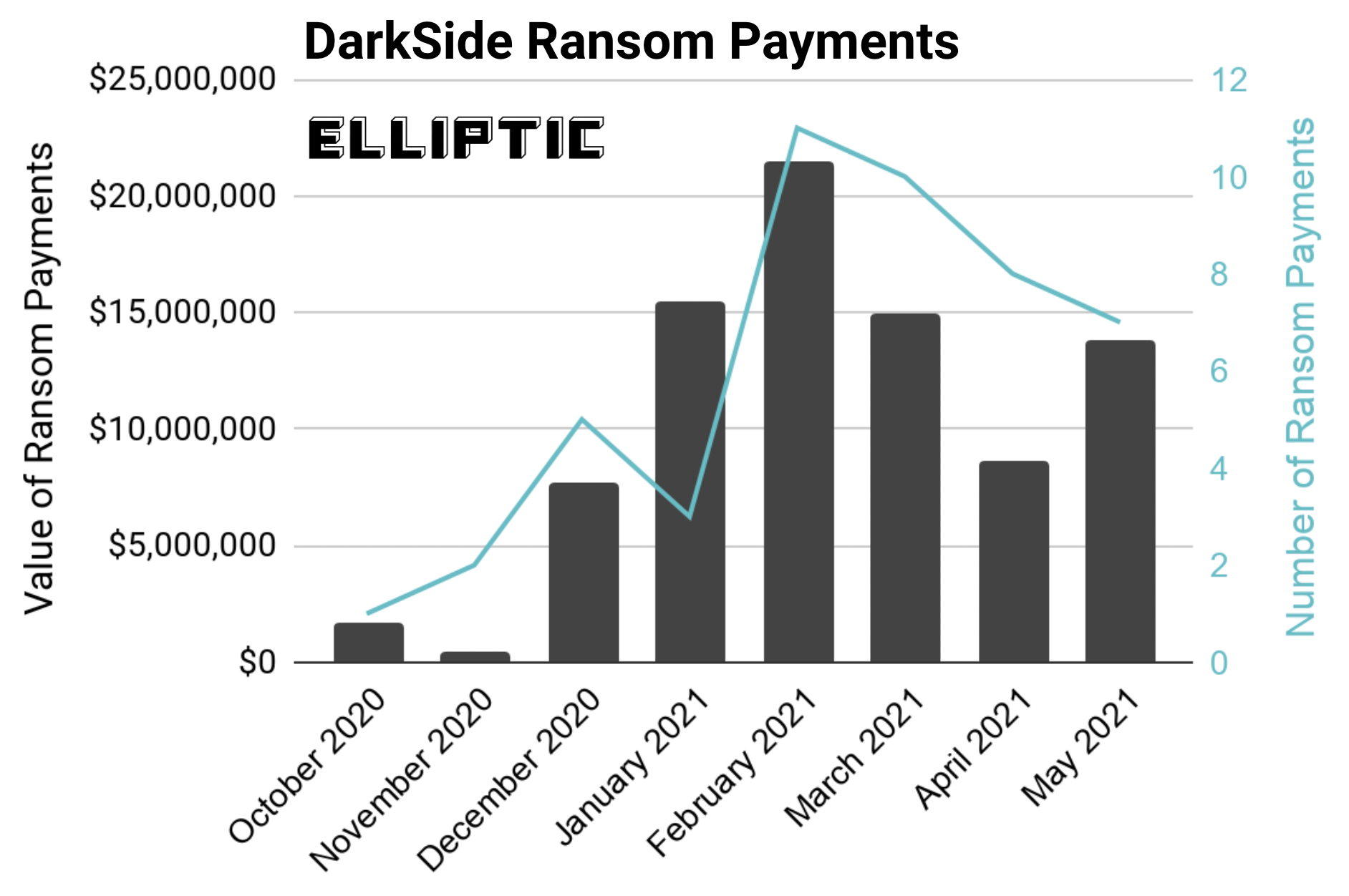
This year hackers got a brand new opportunity to get richer based on Covid-19 hype. McAfee detects more and more criminal attempts to exploit current events. This is why organizations and businesses have to be aware and understand what new attack methods are used by cybercriminals in the Covid-19 world.
Phishing letters now became the best tool for cybercriminals. The amount of such content has considerably grown over the past few months. Users get faked letters as if from the World Health Organization about sales of masks and medications, coronavirus tests, and other medical merchandise (subject of such a message would usually be the most relevant for the addressee from a specific region).
Phishing letters either contain links to sites with malicious content or to documents with exploits or malicious macros. The goal of these activities is to get malicious code to the workstation with the purpose of stealing user or payment data. Hackers also try to lure the victim to a faked web resource with such phishing letters.
The criminal website would imitate the appearance of the bank site or payment system where users are offered to enter personal data. Crypto extorter, cyphering the victim PC, deleting shadow file copies, and demanding ransom is one more variant of malicious software. It is well known, that today most attacks are conducted not by humans but by autonomous software solutions, collecting information about victims from different sources and sending phishing letters automatically. Information needed for such attacks is often collected from social networks and other open sources, which demands practically no effort from criminals. For instance, in user files metadata, which is often in open access, there can be found email addresses, IP addresses, OS versions, etc.
This is a very often occasion when hackers use previously stolen user databases to launch attacks. Criminals may deploy any new attack within just several hours, based on social engineering techniques and the emotions of potential victims. The best defense from such an attack is awareness and informing company employees of cybercriminal methods.
Nexoya Technologies will Secure your networks, applications, server, and devices from hackers, and you should be aware of its weaknesses. we provide the necessary level of security to any type of software, application, server, and device. Our penetration tests allow you to find those vulnerabilities before attackers do.
Don’t worry about cybersecurity – deliver these worries to our experts! We offer high-quality penetration testing services for as long as you need.